Commands run on bash prompt can output content to standard output (STDOUT) and standard error (STDERR)
If you wish to suppress some data, it can be done by redirecting content from either sources to /dev/null. Alternate notations for the above are :
STDOUT = 1
STDERR = 2
/dev/null refer to the Null Device File that discards all data written to it (http://en.wikipedia.org/wiki/Null_device)
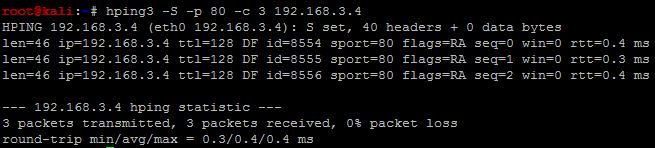
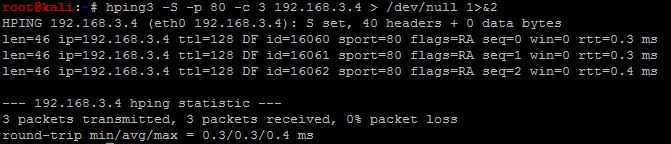
Taking the example of hping3, we can see different outputs as below
The default output of hping3 is sent to both STDOUT and STDERR. The ping responses are sent to the STDOUT, whereas the packet summary/statics is sent to STDERR
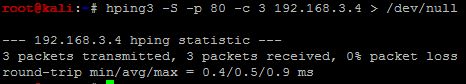
When we send the output from hping3 to /dev/null, only the STDOUT is sent to /dev/null. The other part of the output is not sent to /dev/null as it is actually sent to STDERR
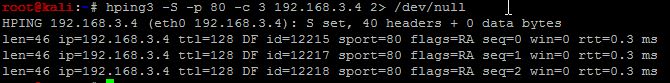
If we want to send the STDERR to /dev/null, we can do the same using the notation 2> . As mentioned earlier the integer notation for STDERR is ‘2’. Thus ‘2>’ represents redirecting STDERR to non-standard location.
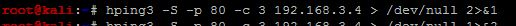
If you don’t want any output from a command, you can simply redirect STDERR to STDOUT which in-turn is redirected to /dev/null
If in some weird use-case you wish to push everything to STDERR, it can be done using 1>&2
Knowing how to redirect STDOUT and STDERR is very useful when scripting in bash.